
WiFi used to be looked at as a luxury, today it’s an expected and fundamental utility required across every industry. From healthcare and retail to education and manufacturing, every business requires secure WiFi connectivity.
Expectations are on the rise and businesses are being forced to support more types of mobile devices in greater numbers than ever before.
We’ve been engineering, deploying and managing large-scale, secure WiFi networks for a long time, 11 years to be exact, and the truth is, things have changed a lot.
Wireless has become increasingly more complex and even more difficult to secure.
When we started, we were dealing with all windows-based, Microsoft machines, and we built our infrastructures to control everything.
We owned the devices and we controlled what went on those devices, however, when the iPhone came out and later Android devices, the way we built our networks completely changed.
After 11 years and over 1,000 deployments, it’s safe to say we’ve learned a lot about wireless and security.
In the blog post below, is an overview of what we’ve discovered from our experience.
Secure WiFi is a system
The quality of your WiFi doesn’t hinge on one component alone, rather a wide-variety of network infrastructure components that must be engineered just right to achieve the best results.
We know that it’s easy to get fixated on common components like access points and bandwidth, but the reality is by doing so, you’re setting your business up for serious wifi problems and worse, frustrated end-users.
What does the system or solution look like? What components are involved? To give you a high-level overview, here is a graphic of how the solution breaks down:
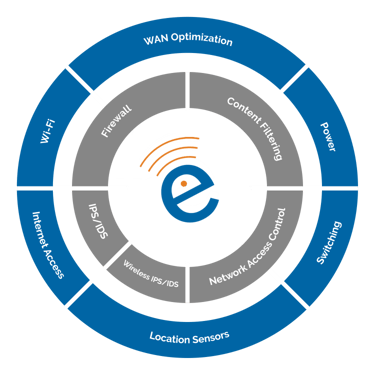
Security is the foundation of your wireless system
In the past, we tried to literally control every device that was on our network and that’s how we approached and enforced network security. It was to the point that we might even physically scan each new device as it hit the network.
To do that today, you’d have to literally load something onto each device, and if you don’t own those devices then this becomes very difficult to do.
So, how do manage the security of all the different types of devices that are accessing your network at the same time?
The way we architect your network security infrastructure today to deal with devices that you don’t own is by building it to manage the risk and the behavior of the devices accessing your network.
Then your infrastructure needs to provide you with visibility into what those devices are doing so you can monitor and take action against those devices in the event of a security breach, or when any abnormal behavior is detected.
There are many components that allow us to achieve these results and one of them is called network access control.
Network access control, sounds like exactly what it is; NAC secures your wireless system by allowing you to see and control who, what, when, where and how your end-users are accessing your wireless network.
NAC does this by identifying, assigning, and enforcing various security policies based on pre-determined roles.
You need a mobile-first network
Wireless systems today must evolve at a very rapid pace.
Why?
Mobile devices (primarily Apple and Android devices) have a refresh cycle or “lifespan” of 12-18 months, before a newer version hits the market. After two refresh cycles the technology has completely changed, which means your wireless system at best will have an effective lifespan of 3-4 years, at which time it will need to upgrade.
Your wireless system needs to be mobile-first, meaning for starters, it has to be engineered to interact with mobile devices, second, it has to secure every device even the ones you don’t own and third, it has to keep up with how fast those mobile devices evolve.
Technical resources are hard to find and expensive
Wireless systems have grown to be increasingly complex. To manage it properly requires three critical elements:
- Specialized skill-set with a long-list of certifications
- Experience
- Time
When we look at the thousands of networks we’ve engineered, installed and managed over the years, roughly five of those customers have had an on-staff, high-end wireless and security resource, not two or three but one.
We’ve realized that producing someone at the necessary skill level is a very expensive and time consuming process.
To make matters worse, even if you could afford to train someone to the required level you wouldn’t be able to keep them on staff for very long because of the low supply and high demand for such a specialized position.
From our experience with even some of the large-scale networks, it’s less expensive to purchase the infrastructure and managed support on the infrastructure than it is to pay for one Wi-Fi and security engineer.
We must measure performance
Secure WiFi is a dynamic environment. From devices and applications, to security threats, usage and even the RF environment itself, everything is constantly changing.
What we’ve learned, is to ensure your end-users are productive, safe and happy we must monitor what the end-user is seeing or experiencing.
With the software that’s available today, we can turn our networks into giant sensors where we can run tests and gain deep insights into what the end-user is experiencing.
It’s important to understand that once you’ve installed your wireless system and start monitoring and getting feedback your system is going to change and need adjustments.
There are more and more devices that are going wireless and finding their way onto your network. This creates security risks and interferes with what you already have in place and if you’re not monitoring things on an on-going basis, you’re going to get behind.
We look at wireless and security as a living and breathing system that requires constant monitoring and management to allow you to always ensure your end-users are receiving the best experience possible.
Closing Thoughts
Like a lot of other types of technology today, you want to be able to budget for wireless on an on-going basis; purchasing your Wi-Fi infrastructure as a service and then buying the resources around it.
For us, our company relies on cloud based applications and software that’s not hosted by ourselves, so if our wireless infrastructure goes down everything comes to a stop and we can’t operate. The same thing can be said for more and more businesses today.
Wireless is a mission-critical service, just like other utilities such as power, and because of this fact you need to manage it with service level agreements.
We like to use the analogy of purchasing a car. If I buy a car and pay it off in 4 years I still feel great about it because now I own the car, and although it might not have the latest features it still runs great. That model is perfect for buying cars, but for buying technology this isn’t the case.
Technology has a specific lifecycle where it functions at its best and if you try to push it past that lifecycle it starts to break down and doesn’t perform well.
If you try to push your wireless network past the 3-4 year mark the user experience is going to suffer and you’re going to get a lot of complaints.
The solution is to get a subscription that fits the lifecycle of the devices or products your supporting. If you own your wireless system, yes you might not have any payments but what you now own at the end of the lifecycle isn’t worth anything.
With WiFi as a Service or a managed WiFi subscription, you can scale as your needs evolve up or down, as well as upgrade alongside the technology as it changes so you always have the latest system in place.





