
We don’t like to brag, but at SecurEdge Networks, we really have thought of everything necessary to provide you with fast, reliable, and secure WiFi. Not only that, but we’ve bundled it all together into a comprehensive monthly subscription package called SecurEdge WiFi. Okay, maybe we do like to brag a little.
Over the next two blog posts, we want to let you peek under the SecurEdge WiFi hood and get a feel for our proprietary services process that's included with WiFi as a Service. In this post, we’ll focus on the first two steps, analysis and design. Then in part two, we’ll talk about our methods for deploying and supporting wireless networks.
You’ll notice that the common thread running through this discussion is security. We beat the security drum often because it’s the foundation for everything we do. It’s in our name and in our company’s DNA. So, we’ll keep coming back to security in this post.
Analysis
Before we can determine the types, amounts, and placements of physical hardware, we need to do our homework. And although we’ve been doing this a long time and in many cases have a good idea of what will be required before we take a closer look, there really is no one-size-fits-all approach when it comes to proper WiFi design.
There are so many variables that can affect the performance of your wireless network, and it’s our job to identify those variables so we can tailor a wireless LAN solution to your specific needs. These variables fall under five main categories, with lots of interplay and overlap between them:
- Industry - The needs of a college campus will be very different from those of a warehouse, or a hotel, or a medical facility. So, we’ll start by looking at the historical data we have collected from years of deployments across virtually every industry to start thinking through your industry’s particular WiFi needs and challenges.
- Coverage - The physical layout and makeup of a space can affect RF performance, so at a minimum we need to know the size of your environment in square feet. However, while square feet can get us started, we might need to ask for floor plans. Gathering this information will help us understand if there are things that will cause RF interference, such as building materials and any possible physical obstructions.
- Devices - We need to get a sense of both the number and type of devices that your network will need to support. Beyond the obvious computing and mobile devices (e.g., laptops, tablets, smartphones) are many other specialized devices (e.g., temperature sensors, medical devices, IP cameras) that may be unique to your business.
- Users - We’ll want to know who will have access to your network, and how many of them. Will it be employees using corporate devices, their own personal devices, or both? How many guests will be accessing your network? Understanding your user base allows us to plan for the security of their devices and your network.
- Applications - This ties into the previous points. The specific applications your network will be supporting largely depends on your industry, users, and their devices. College campuses will need to support a lot of video streaming, email, and social media; retail is dependent upon PoS (point of sale) systems; hospitals might rely on asset tracking; and warehousing might need inventory management systems. We might even need to assist in the implementation of custom applications for you, and this can all be done as part of our end-to-end subscription package.
Design
Once we’ve gathered the necessary data and have a solid understanding of your WiFi goals and requirements, we can then design a reliable, secure WiFi network that will provide you with optimal performance.
Every design we do flows out of our secure mobility stack (see graphic below), of which security is the foundation.
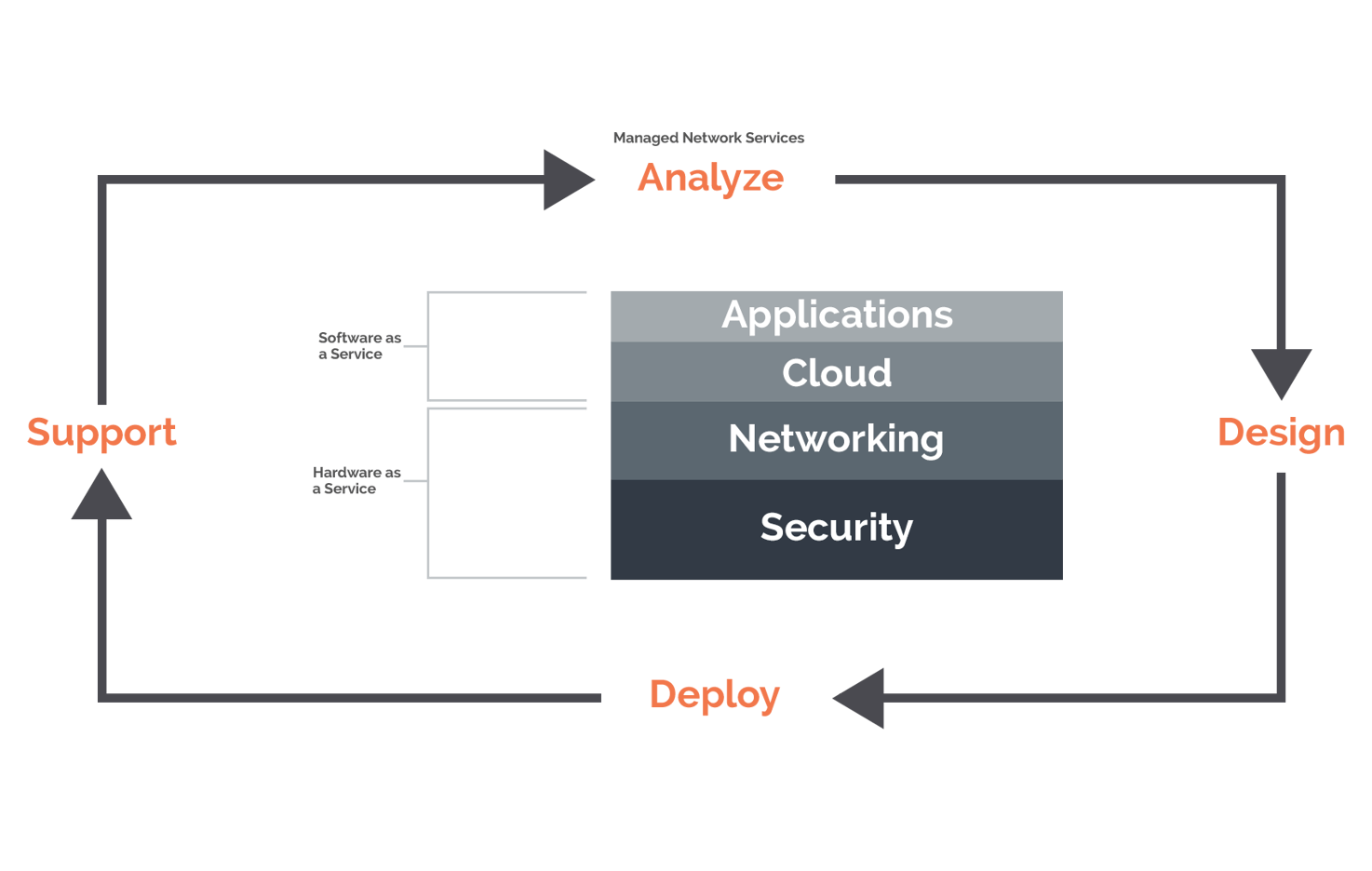
How do we onboard devices and register new users? How do we protect your network from ransomware and your users from having their data compromised?
Then we move to networking, which includes all of the physical hardware we need to put into your space (e.g., access points, wifi switches, wifi controllers).
Then we add our proprietary cloud software that we will use to manage your network, and finally, we tailor the design to accommodate any add-on applications you might want to use, such as wayfinding, asset tracking, emergency notifications, location services, and so on.
*Note: All predictive designs and/or basic estimates will need to be validated by a more detailed wireless site survey to allow for adjustments that the real-world environment might reveal.
It’s important to point out here that unlike a blueprint for a house, the design for your network is not static.
Pouring concrete and stacking bricks are relatively permanent acts, but a wireless network is more like a living thing. It will have to change over time, for two main reasons:
1. All of the variables discussed in the Analysis section above can change—and most of them will.2. Technology has a shelf life, so your system will need to continually upgrade alongside the fancy new devices that will be connecting to it.
These are two of the many reasons why partnering with a managed WiFi provider like SecurEdge brings so much value to your business.
To Be Continued...
One final thought on analysis and design: when we design a network for your business, we’re factoring in all of the built-in capabilities for the ongoing management and maintenance it will require. We’ll dive deeper into the deployment and management side of things in our next blog post. Stay tuned!





