Pop quiz: What do Under Armour, eBay, Target, JP Morgan Chase, Home Depot, and Uber have in common?
Disturbingly, these large, highly recognizable, well-respected companies have all fallen victim to massive security breaches just in the last five years. And the damage in each case has been profound. In Target’s case, profits fell 46% within two months of the company’s announcement of the breach.
Compromised Data
The JP Morgan Chase breach affected 83 million household and small business accounts, and the New York Times later reported that it could have been prevented with a simple security fix. Apparently one network server hadn’t been upgraded to using two-factor authentication. That one overlooked security fix led to 83 million accounts compromised. That’s a real kick in the seat of a security team’s pants.
It’s also a lesson learned: determined hackers will find any vulnerability, any unlocked back window, and slip their way in. And when they do, it can be devastating for a company and frustrating for its customers. Furthermore, if it can happen at the largest bank in the United States, it can happen anywhere.
Credit card numbers, dates of birth, passwords, bank account numbers, addresses, phone numbers—all of this information and more becomes vulnerable when a company’s network is hacked. Customers tend to be turned off when they perceive that a company hasn’t properly protected their privacy. Profits, stock prices, and a company’s reputation all take a major hit in cases like these. And the costs associated with upgrading network infrastructure to prevent the same thing from happening again make a security breach a double hit.
Time for Change
Enterprise security is changing rapidly, largely due to the rise of big data and cloud computing. The past decade has seen more and more applications and sensitive data move to the cloud. Companies need to ask: Is this data being stored, accessed, and transferred securely? If the answer is no, or it’s unclear, then the next question needs to be: How do we fix that?
Companies that don’t have a future-facing enterprise wireless security strategy will find themselves vulnerable to breaches, putting their own internal data and that of their customers at risk.
Fortunately, a rising number of company board members, risk management experts, and key decision makers are acknowledging the need for better enterprise cybersecurity, prioritizing it, and seeking out solutions.
Getting Serious about Security
It’s important to identify and secure the various points of vulnerability when strategizing enterprise security. Don’t overlook your wireless network security.
Creative hackers will use all sorts of tactics to try to get access to a company’s wireless network. They can be clever, but a capable wireless network provider can ensure there are barriers to protect your network and alerts to let you know as soon as a problem arises.
It’s no coincidence that the word “secure” is in our company name. Security is the foundation for everything we do at SecurEdge, and we always say that a network is only as good as its security. It’s the primary consideration for every enterprise wireless network we design and for the ongoing network management services we provide.
We build wireless security solutions that protect enterprise wireless networks from malicious attacks. Our approach to security threats is multi-pronged: prevent, detect, identify, and contain.
Our wireless security solutions include :
- intrusion protection
- rogue AP protection
- automated scanning
- location tracking
- compliance reporting
Our software gives network administrators real-time visibility into their network and every device connecting to it. And our solutions are totally customizable, depending on your organization’s needs and security levels. Simply put, we help equip those who need access to your network, and block those who don’t.
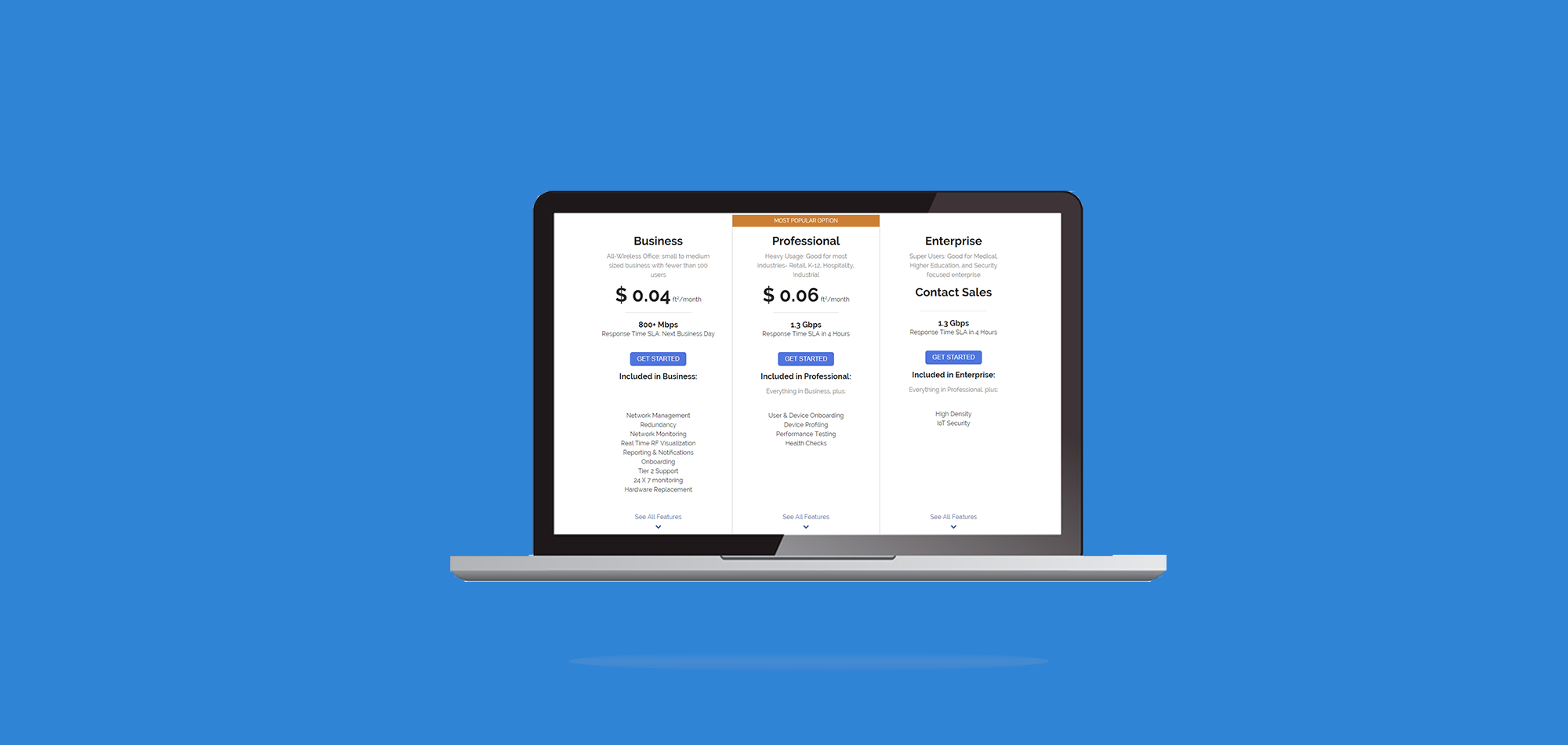
This kind of industry-leading wireless security sounds expensive and complex doesn’t it? Using SecurEdge Cloud, our network subscription software for businesses you can get the network you want, how you want it—including proper network security. We include role-based access control with every subscription as well as the latest network security best practices, hardware, and software. If you're interested in a network subscription, use our business WiFi pricing tool to get a price in minutes.
Network security can’t be ignored, done halfway, or pushed back on the agenda. The risks are too high. Hackers aren’t picky about industry type, company size, or geographic location. Every company that lapses on cybersecurity could be the next one added to the list at the beginning of this blog post.