Overview
Your challenge is to provide a fast and secure wireless solution that will support your business and it’s end-users year after year.
Did you know? Today’s wireless networks have a useful shelf-life of 3 to 4 years
With technology changing at such a blistering and unforgiving pace, you need to always have the right wireless system in place to maintain proper performance and a productive user experience.
This document will give you some things to consider before you select the infrastructure components and put together your wireless deployment plan.
We’ve compiled this information from over 12 years of experience analyzing, designing, deploying and supporting large-scale wireless systems (we consider large-scale to be 100+ access points) across every industry.
There’s a lot to cover, so let’s get to it!
Radio Frequency (RF Planning)
The first thing to consider when deploying wireless is regarding radio frequency or RF and where you want to provide wireless access.
It’s not as easy as just broadcasting a strong signal for devices to associate (connect) to.
In large-scale environments you’ll have many different types of devices, users, and areas to cover. It’s also important to consider how the Wi-Fi is being used in different areas of your business.
Are people streaming video or simply using email? Are they using Skype, a PoS system or taking inventory using RF guns?
To get the best results you’ll need to consider three key things:
- Coverage
- Capacity
- Performance
Coverage
Coverage can be defined as the areas where you want your end-users and devices to be able to attach (connect) to the wireless network. It’s important to answer these two questions:
- Where do I need RF coverage? Indoors? Outdoors? Both?
- How much throughput (bandwidth/speed) do you want to set as your benchmark?
One of the first pieces of information we’ll need to collect is the size of your building or buildings in square feet. Often times we’ll also need floorplans or blueprints when planning for coverage.
Planning for Capacity
Each wireless access point can handle a certain number of wireless clients or devices connecting to the network.
This means that you need to consider the areas that may present a high number of users. Typically, the more users in a particular area the more important that area should be considered.
Often, an organization will overlook things like classrooms, large meeting rooms, nurse’s stations, etc. These are high user-density areas that present major issues if not planned for properly.
Performance
Knowing a little about your RF environment will go a long way in helping to plan an optimal WLAN. This is where a site survey can come in handy.
A site survey will uncover RF occurring already in your environment and advise accordingly.
For example, if your environment is already saturated with 2.4 GHz RF then moving your devices/end-users to the 5 GHz spectrum might be advantageous.
Also knowing how much bandwidth will be needed to accommodate your devices and applications that will be using the WLAN is also important.
With 802.11ac offering the highest levels of performance and scalability, it’s advised to explore going with high-speed rather than legacy Wi-Fi products.
Never try and use access points (routers) that were made for residential environments. They are not the same as enterprise grade hardware and will be a waste of time and money.
Applications and Devices
Proper Wi-Fi planning means having as much information as possible, and then understanding what to do with that information to create an optimal design.
Knowing how many devices will be accessing the network, what types of devices there will be and what applications be running on the system are critical elements of every successful design.
Voice and video are two very demanding applications for a wired network much less a wireless one. Knowing the resource requirements of these and other applications intended for the WLAN will provide useful measurements for the planning of the network.
If you’re reading this, then you are most likely planning what we call a “multi-media grade” WLAN, which is to say you need the system to handle anything you want to put or allow on it.
We recommend creating a list of applications and devices you’ll need to operate on the network and assigning an order of priority to the applications and devices.

The system should be engineered to support the most mission-critical applications first.
For example, your nurses’ wireless VoIP phones will take priority over the wireless internet access for your guest users.
Security
In the past, wireless security was considered to be inferior to wired security. This is no longer the case.
Things have changed dramatically over the last 10 years. We’ve gone from trying to physically control the few devices accessing our networks, to having no control at all, i.e. BYOD.
With the release of smart phones and soon after tablets, the mobile age was finally here—and with it, a much more difficult wireless landscape to secure.
There are two main challenges:
- How do you secure what your business doesn’t own?
- How do you secure the different types of devices on your network?
Today, it’s about a multi-layered approach where the goal is to manage the risk and control the behavior of each device that’s accessing your network.

Then your infrastructure needs to provide you with the visibility into what those devices are doing, so you can monitor and take action against those devices in the event of a security breach, or when any abnormal behavior is detected.
Wireless is a system; there are many components needed to achieve the best results.
Let’s take a look.
Wireless Intrusion Detection Prevention
(WIDS) is very helpful in being proactive with wireless security. An integrated WIDS system in your wireless network can detect and prevent varying degrees of attacks and hacks that are used to acquire access to your network. It is also useful in something as innocuous as the dreaded “Rouge AP” which is installed by well meaning, but poorly informed employees seeking to gain mobile freedom in the workplace.
Network Access Control
(NAC) is security software that integrates with both your wireless and wired infrastructure to do exactly what the name implies — control access to your network resources and the internet. At it’s core, network access control should do two things: Role-based access control and Policy enforcement.
With role-based access control (RBAC) you will have the ability to assign specific rules or policies to either an individual user or a group of users that are connecting to your Wi-Fi network.
Policy enforcement or endpoint security/compliance allows you to assign and enforce a specific security policy to your end-users based on the roles you’ve assigned them earlier using RBAC. This allows you to further control the behavior of the devices accessing your network whether you own them or not. Policy enforcement protects the user, your other users, your business and even your job by preventing them from accessing non-approved content, downloading a virus or spreading that virus across your network.
Directory Services Integration
Integration with your directory services is a critical step to provide wireless security by being able to authenticate each user connecting to the network. The credentials created for each person inside your directory services should also be used to authenticate the user on the wireless infrastructure so that you have one database of users accessing the network.
Next-Generation Firewalls
Your wireless system needs to be able to segment traffic by user groups similar to the way a LAN firewall segments VLANs.
For example, a guest user should be denied all internal servers and only be able to access the internet gateway to surf the web and check email.
What’s more important, the port someone is using or the application they’re using while online — chances are you’re more concerned with the application. Next-gen firewalls today allows businesses and IT teams to have granular visibility into the applications and traffic, instead of outdated practices such as ports and IP addresses.
Next-gen firewalls are essential for end-to-end threat protection, and a security solution that is more cost effective and less complex to manage.
Network Infrastructure
The following items are important pieces to the success of any wireless network implementation. Knowing what they are and why they’re important to have in place will ensure an optimal wireless experience for your customers, employees and guests.

Switching
New 802.11AC access points have potential for Gigabit speeds, however, if your edge and/or core switches aren’t up to date or compatible then you’ll never reach the speeds you were expecting. We advise and recommend at least 1 Gigabit switches at the edge and 10 Gigabits at the core, preferably with PoE+ for connectivity with your access points.
DHCP DNS
Static IP networks can present issues with access point and wireless client functionality. It is advised and preferred to have a dynamic IP network. Static IP networks can work but will prove in the end to be an administrative headache. Locally hosted DNS is also preferred as your access points will be dependent on name resolution to find their controllers over layer 3 networks. If your network is a flat layer 2 network then this is not as crucial.
PoE Power
Access points can be powered by PoE (Power over Ethernet) which makes the installation of cabling to the APs very clean and eliminates the need to have AC power locally at the access point location. Surge protected power will be needed at the location of the PoE adapters or switches that are providing power to the APs. A managed power solution like the one found with SecurEdge subscriptions provides the ability to remotely restart your system.
System Management
One of the biggest challenges with enterprise-grade Wi-Fi comes after you’ve installed it and turned it on.
Managing your wireless network is a full-time, 24/7, 365 days a year job, and it’s why we say that wireless is a never-ending process.
There’s a couple reasons for that statement.
- Wireless is alive-It’s constantly changing. From your devices (BYOD, the IoT) and your end-users, to usage, applications, security threats, and even the RF environment itself—everything is constantly evolving.
- Technology changes rapidly– Mobile devices have a refresh cycle of about 12-18 months (sometimes 6 months if you always want the latest device). After approx. 2 cycles these devices will have completely changed requiring your network to keep up with the new capabilities and operating systems found on those devices.
Even if you have an optimal design, using high-quality hardware (infrastructure) components, it takes the right software and a highly-skilled network engineer to properly maintain the performance and health of that system.
The biggest challenge with an enterprise-grade wireless implementation (especially large-scale deployments) is trying to manage both the amount as well as the different types of devices and end-users that are accessing the system after it’s been installed.
Wireless is dynamic—it’s alive and everything is changing all the time. Here’s a short list of what you can expect to change after you’ve implemented your new system:
- Devices
- Applications
- Usage
- Security Threats
- even the RF Environment
To keep your network operating at optimal levels, and more importantly your end-users happy and productive, then you have to measure performance from both the perspective of your wireless network and what your end-users are experiencing.
Support for any secure Wi-Fi network is a never-ending process as illustrated below.
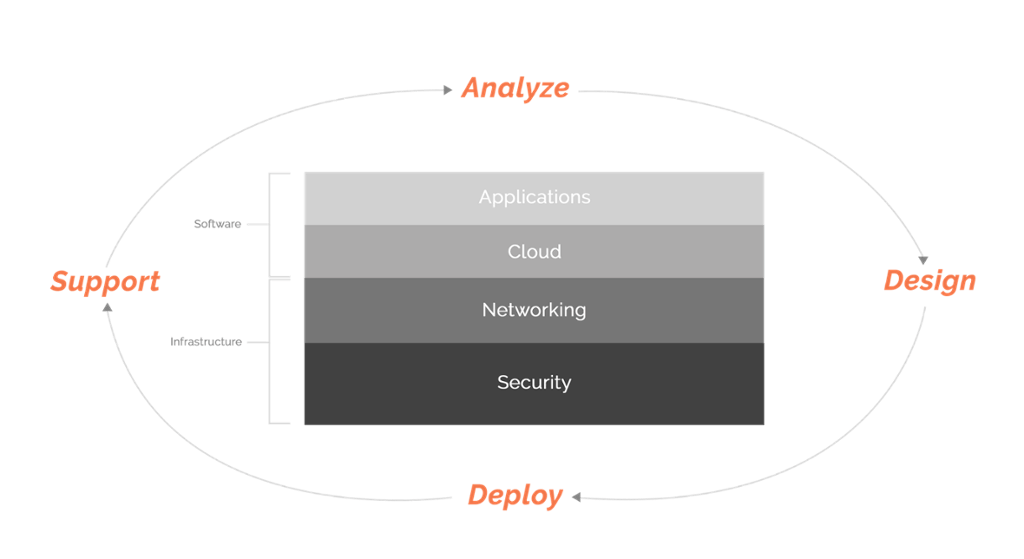
You need the ability to see everything that’s happening on your network in real-time and on an on-going basis. This will allow you to be proactive when it comes to making improvements, troubleshooting problems and even with providing compliance reporting if necessary.
We suggest varying levels of management based on several criteria and the needs of the organization, but here is a basic starting point.
User and Device Management
You need to be able to assign “Bandwidth Contracts” to users and/or devices. A policy might be: each user is assigned 1Mbps of bandwidth from 8am to 5pm but 3 Mbps of bandwidth per user after 5pm.
Adaptive Radio Management
RF is dynamic; your system should also be dynamic. ARM uses the access points (APs) deployed in a facility or campus as sensors for providing feedback about the RF environment and then uses that feedback to make intelligent decisions about setting power levels, channels and adjusting client loads. ARM basically becomes your RF expert to help mitigate some of the issues that are experienced in the dynamic RF environment all WLAN installations re exposed to.
Change Management
In the old days, you had to configure each access point on your network separately (can you imagine managing just a 50 AP network?). Today, you can configure one management console and then push the configuration out to every AP. Likewise, you should also be able to grow the wireless network simply by installing a new AP and having it join the WLAN automatically.
Help Desk/Administrative Access
There should be an option to set up levels of access for the management interface. Guest provisioning should be handled by administrative staff or help desk users. But write access for the major system configuration should come with high level privileges.
Reporting and compliance
Process logs, device level reporting, trending, network monitoring, RF health, alerts are all ways to proactively manage your WLAN and your management system can provide them.
Scalability
Whatever solution you choose will be able to easily accommodate your future wireless growth.
In our experience as soon as you introduce wireless to your users they will want it everywhere.
When planning take into account a full campus or wireless everywhere plan even though you may only have the budget for a few select locations.
This will give you an idea of how big you may need to grow and what solutions can achieve this and accommodate your future needs.
Location-Based Services
A location-based service, often known as Real Time Location Services (RTLS), is the ability to physically locate a user or device on a wireless network.
Think of it as GPS inside a building. There has been considerable debate about whether a Wi-Fi Network can handle the capacity of RTLS and if it is accurate enough to locate a device within a reasonable distance.
 The answer to the capacity question is that the right platform can easily handle the load as the data traffic from a WiFi-enabled RFID tag is very minimal.
The answer to the capacity question is that the right platform can easily handle the load as the data traffic from a WiFi-enabled RFID tag is very minimal.
As for accuracy, the system uses wireless access points to “triangulate” on a user or device, so the more access points are deployed, the more accurate the system will be.
If considering RTLS, we recommend defining how accurate you need the system to be, for example: within 20 ft., then having a wireless company (like us) help define how dense an access point deployment you may need.
Redundancy & Reliability
Wireless when implemented correctly will quickly become your user’s main means of connectivity and they will become reliant on it, HEAVILY.
Because of this it will be important to you and your users that you have ensured High Availability for your WLAN.
In order to achieve High Availability you will need to build in redundancy and other means of reliability for the system.
For many of our customers who are hospital systems or college campuses, if the system goes down, critical functions are interrupted (quite literally in the hospital wireless network).
Consider the cost of downtime and how it will impact the organization during the design process. Then work with an expert to design as much high availability into the system as necessary.
Warranty Support
One of the most critical steps to building a reliable wireless system is making sure you have the proper level of support to meet your requirements.
Murphy’s Law of critical systems is that something will go wrong eventually. (For Example: Last year one of our hospital customers had a water pipe break directly above a data closet housing a critical part of their WLAN system.)
Here are some things to think through to make sure you’re ready:
Hardware/Software Replacement
Your wireless network will have many different component parts. You need to understand what happens if something fails or is damaged.
- How long is the warranty on the wireless network components (access points, antennas, software, etc.)?
- How quickly can you get replacement parts?
- How will they be installed when something does go wrong?
- How does the system react/adjust to a component failure?
- What is involved in adding the replacement to the network?
Support
Being able to get an experienced engineer on the phone to help handle critical support issues is a vital asset to maintaining a large scale wireless network. Support specialists should understand your specific requirements and be able to respond and resolve issues quickly.
Maintenance/ Managed Services
Your wireless network will have software and firmware that needs to be updated and maintained on average of once per quarter. We call this a quarterly refresh of the system to keep it up to date and ensure that the system has the latest security patches and updates available.
This can be a tricky process because with typically each new release, it brings additional features and potentially, additional bugs in the software.
Consider utilizing an engineer that is an expert on that particular platform to assist with issues or even provide the service ongoing to free up your internal resources. Many times utilizing an expert on a monthly or quarterly basis is more cost effective than figuring things out internally.
Pre-Design Data Collection Worksheet FAQs
Proper Wi-Fi design and planning is all in the details. Filling out the Pre-Design Data Collection Worksheet below is a great first-step in the design process, and it helps guarantee that nothing gets overlooked.
Wi-Fi is very complex to navigate correctly and over the years we've been asked a lot of questions regarding the process and what to expect.
Below is a collection of the most frequently asked questions we've received.

