
So, you are planning your next adventure to a far away land. You’re scanning through your tablet’s browser looking for cheap flights to your desired destination. While downloading the best mobile travel applications, you are also texting your travel companion with thumbs spinning so fast, you start kicking up more dust than the jeep you will be driving in on that safari.
OK, maybe this is a bit much for this week’s blog post on securing your enterprise’s mobility system. The point (hopefully) is we can spend a few minutes together, comparing the preparation of your wireless network infrastructure to a survival situation. If on that trip you get separated from your group, at some point you will have to start preparing a shelter. Just like you might consider four walls of defense on the first of what could be many nights, you’ll also want to defend your digital village with a firewall built for the next generation.
Scan Your Surroundings and Your Network
The first step in any survival situation is to get a sense of your surroundings. You can live for a few weeks with no food, but just 3 to 5 days with no water. The death of your wireless network may take less time, if the appropriate infrastructure is not in place to support your efforts. Any number of factors can bring down a network, and leaving your wireless network exposed to today’s digital attacks is like being in the middle of the rainforest, swinging from vines, covered in bunches of bananas. Just like that kind of monkey-ing around would be a bad idea; it would also be poor judgment to have a lack of awareness of your surroundings. Specifically, the applications running in your surroundings which have been given “permission” on the network should still constantly be scanned for viruses and malware. Many infected documents are stored in collaboration applications, along with some documents that contain sensitive customer documentation that should not be exposed to the outside world.
Threat Management
Want to ward attacks by those hungry internet lions hidden on the web? Then don’t rely solely on that prickly, thorny little rose bush surrounding the perimeter of your network to protect you from attack. Threats don’t just come in through specific “ports” these days. Traffic from your mobile device users must be brought onto the network safely. That’s where today’s Next Generation Firewall solution from Palo Alto Networks provides always-on VPN connection, which complements firewall protection. The always-on VPN connection to the network back at corporate headquarters can verify all users have the exact same network policies that they would have, were they physically in the building.
Build a Fire(wall)
If you’re stuck in a jungle, just starting a fire may be an issue. However, you must try to keep your body warm, your water boiled and any meat must be cooked. But, fire prevention in a survival situation is also a big key. Clearly, in your Information Technology environment, protecting your organization from attack (or flame-throwing attacks from cyberspace) is considered your responsibility. So, make sure the protection you put in place is capable of protecting you against today’s threats, which can even come from applications on those wireless devices.
Know Your Applications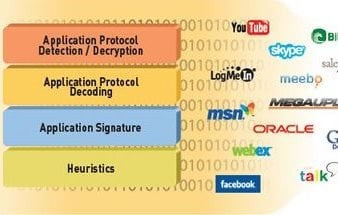
You know how to use a knife for survival, just as you would want to know what other applications are at your disposal - and how to control the digital applications. With rising popularity and declining costs, wireless devices are now more affordable than ever and creeping into the hands of those technological headhunters. With so many different operating systems, application development has become more popular and easier to accomplish. Remember that easy doesn’t always equal good, nor does it equal a safe swamp for everyone to dip their toes into. The dangerous jungle that is application development has taken our fortified shelter and opened the proverbial palm branch door, allowing in less quality control before the apps go to the public market. Since application developers no longer stick to the old standard of port/protocol/application mapping, more applications are now capable of hopping ports like a rodent to his next burrow, or operating on non-standard ports until they pass off their infectious disease to your open wireless network wound.
Identify and Control Circumventors
There’s always something lurking right outside of your base camp, and you won’t know how it might try to harm you until you identify the threat. Sneaking around and sniffing out the situation from a distance, the dangerous tiger is looking for suitable ports of entry. In the same vein, most organizations today have network security policies and controls designed to enforce acceptable use policies like the law of the land. Meanwhile, other more villainous attackers might use proxies, remote access, and encrypted tunnel applications which are specifically used to circumvent security controls like firewalls as they attempt to attack networks. Apparently, stonings no longer work when trying to bring down a wireless network. Seriously though, without the ability to control these circumventors, organizations can no longer enforce their security policies and thus expose themselves to the very attacks they imagined their system controls would prevent. (Be wary if your first line of defenders is the “Knights Who Say Nee!”) A next generation firewall solution should be capable of dealing with these types of circumventors while also regularly updating application intelligence.
Scan for Viruses and Always Carry a Mosquito Net
In a survival situation, you can live for a few weeks with no food, but just 3 to 5 days with no water. The death of a document or function of your business may take less time, if the appropriate infrastructure is not in place to support your efforts. Any number of nasty worms can infect a network, and leaving your wireless network exposed to today’s digital attacks is like being in the middle of the rainforest, swinging from vines, covered in bunches of bananas. Just like that kind of “monkey-ing” around would be a bad idea; it would also be poor judgment to have a lack of awareness of your surroundings. Specifically, the applications running in your surroundings which have been given “permission” on the network should still constantly be scanned for viruses and malware. Many infected documents are stored in collaboration applications, along with some documents that contain sensitive customer documentation that should not be exposed to the outside world. As for your real life survival situation, if you’re going to the jungle, be sure to take an extra mosquito net to shield you from those airborne pathogen-carrying critters.
Write a Policy to Handle the Unknown
Without regular sustenance, the mind can start to wander, so it’s best to write everything down in a journal of some kind to remember your experience. The internet can also make your head hurt, seeing as there is always going to be unknown traffic to deal with and it will always represent significant risks to any organization, large or small (think about how those itty bitty little spiders can bring down a 250-pound human with one bite!) Unknown traffic can be minimized, custom applications can be easily filed so they are “known” in any network security policy, much like tribal markings may have been used to identify “friend or foe”. With your next firewall solution, the appliance must attempt to classify all traffic, which provides a positive enforcement model - meaning that traffic receiving an “approved” marking may pass. Allowing all unknown traffic onto your network would be like allowing anyone and everyone through the front gates of the village and once they’re in, it would be hard to get them to go. As a best practice, “allow all” should not be the foundation of your policy structure at the entrance to your digital village.
Protect Your Remote Villagers as Well
Users are increasingly outside the four walls of your digital village, as they have been assigned to hunt different territories. A significant portion of the enterprise user population is now capable of working from remote locations. They expect to quickly connect with their devices to their applications via WiFi (not available in the jungle) or any other means necessary to complete their job duties. Hopefully, they are NOT forced to use a dial-up connection, which would be as frustrating as trying to send smoke signals from a campfire during a rain storm. Regardless of the location of the user and the network they are accessing (library, home, guest network) the same standard of policy control should apply. If your next firewall enables application visibility and control over traffic inside the four walls of your digital village but not outside, it misses the mark on preventing some of the most risky traffic and flaming arrows!
So while drawing up analogies with network security and your next jungle adventure may be a bit far-fetched, the key takeaway should be that old Boy Scout motto: Always be Prepared. Surviving in today’s digital environment is about as hard as surviving outdoors with no transportation other than your two feet. Being ahead of the curve in knowing how to defend your “digital village” when you find a place to camp out will keep your spirits up until you are “rescued”.
When it comes to firewalls, we recommend Palo Alto Firewall, because it’s a complete solution that contains all the above features. If you would like a free demo or just some more information on Next Generation Firewalls you can contact us here. Also check out the great eBook below for more information.




