The acronym BYOD stands for “bring your own device” and is proving to be many Network Administrators’ new challenge; i.e. headache. BYOD refers to the practice of allowing Employees or Students to bring in and use their own laptops, netbooks, tablets, and phones on the Hospital or School network. Generally this practice is being looked at as a means of alleviating budget constraints at schools since they often are unable to provide each child their own laptop, netbook or tablet. At Hospitals it is being evaluated as a convenience for the Doctors and Employees who want to use their own devices so they can work on them at home and continue using them at work.
This practice opens up a Pandora’s Box of issues that I cannot possibly list completely here. The top issues that come to mind is the security of the network and the devices that the Hospital or School own. When these personal devices are brought in and introduced onto the network they can potentially “infect” the network and the other devices they have access to.
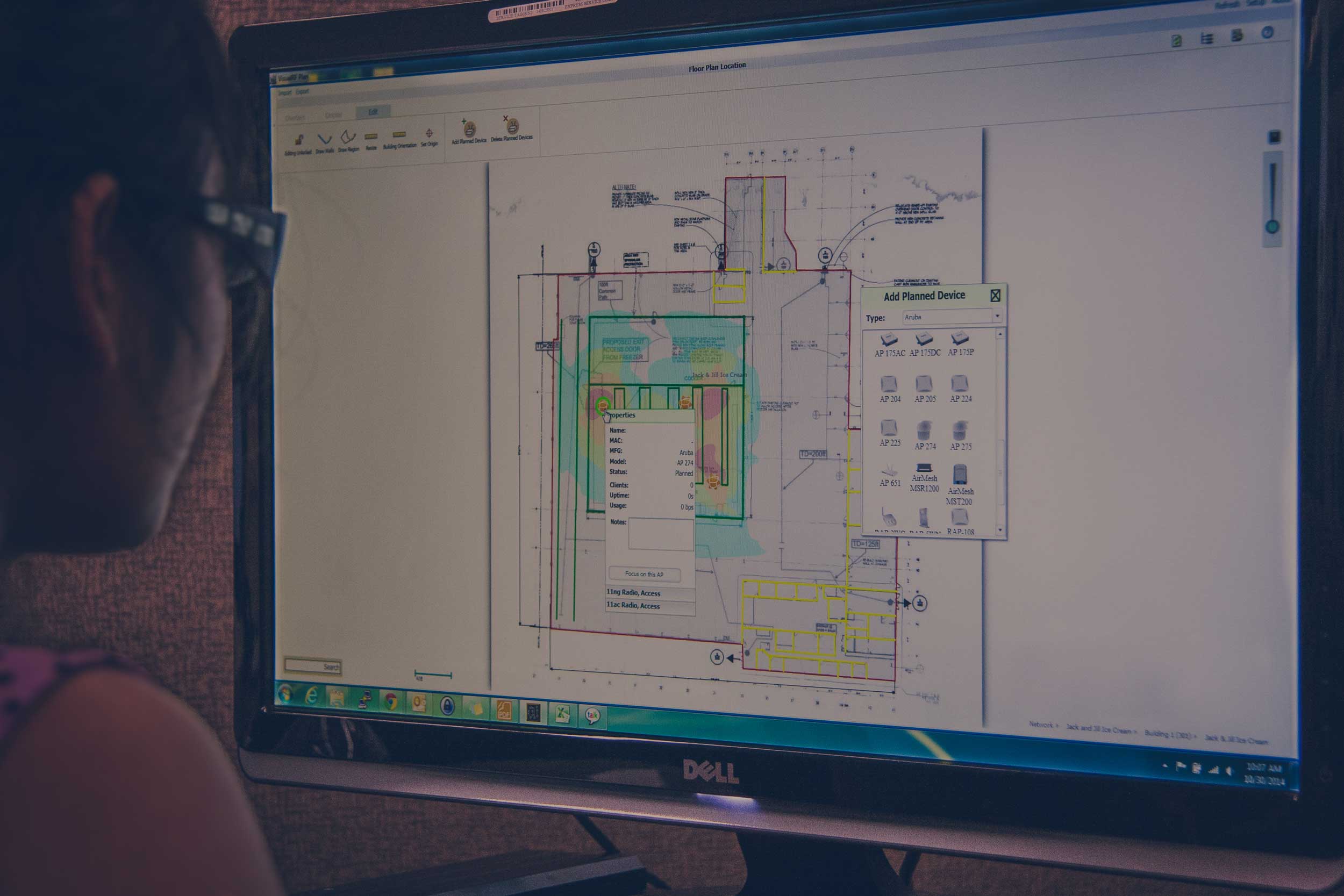
As a Solutions Engineer I am tasked with finding answers to these challenges that our customers are facing and this BYOD challenge is a big one. Luckily our partners and other products that have been introduced recently have seemed to come together to help us create a perfect solution to this challenge.
The products that we use to meet this challenge provide the following functions:
- Role Based Access (RBAC) – by integrating with Active Directory or another directory database that supports LDAP we can assign a role to a user (Faculty, Staff, Student, Guest, etc...). Once we have the role defined we can leverage built in firewall services to apply policies to the role. For instance; Faculty can access multiple network shares, servers, printers, web, and other network resources while the Student role is limited to access to one network share, a limited set of printers and web access is proxied through a content filter.
- Automated certificate provisioning – since the devices that are being brought in are not school or hospital owned assets the ability to push certificates to the devices and use certificate based authentication and encryption is hampered. A product that presents a certificate and installs it on the device once the client has authenticated themselves allows for 802.1x authentication on the network which is the best you can get now.
- Device fingerprinting – this function provides the ability to see what type of device is accessing the network; Apple iOS, Android, Windows based, etc... Applying policies customized for different device types will help the administrator in the long run.
- Application Detection – being able to control what applications are going over your network from these devices is another critical piece of the pie. Sure you are blocking everything except HTTP/HTTPS access but what about those applications that use port 80. If you block port 80 you have cut off internet for everyone. With Application Detection you will be able to allow Facebook but disallow the chat or disallow Skype but allow Google chat with video.
- Threat prevention – removing the threat of viruses and other malware propagating from these devices is a definite must have for any network security. There is not telling what your users are bringing with them from home. With the ability to filter the traffic coming from these devices you can block unwanted malware from hitting your network and spreading to other users’ devices and your devices as well thus preventing a large scale catastrophe.
Don’t bury your head in the sand and hope that this is just a passing phase, it isn’t. New devices are coming out every day and the only way to manage them is to be proactive and get ready to accommodate them. Let us be your aspirin for this potential headache by contacting us to have a conversation about what can be done to avert the disaster.