
Have you logged onto a public WiFi network in a Starbucks or Panera Bread recently? If you have, you’ve seen a log on web page otherwise known as a “captive portal” page. It looks like a standard web page and most people click through the log on process without giving it much thought.
But there are some really important things captive portal pages do that you need to understand if you’re the one offering free wireless guest internet access.
Many times small businesses or even hospitals will provide their guests with free access to their wireless networks without using a captive portal solution.
This can have many negative consequences for both your end-users and your business. From legal issues to your bottom-line, implementing a captive portal will become an integral part of your overall business strategy.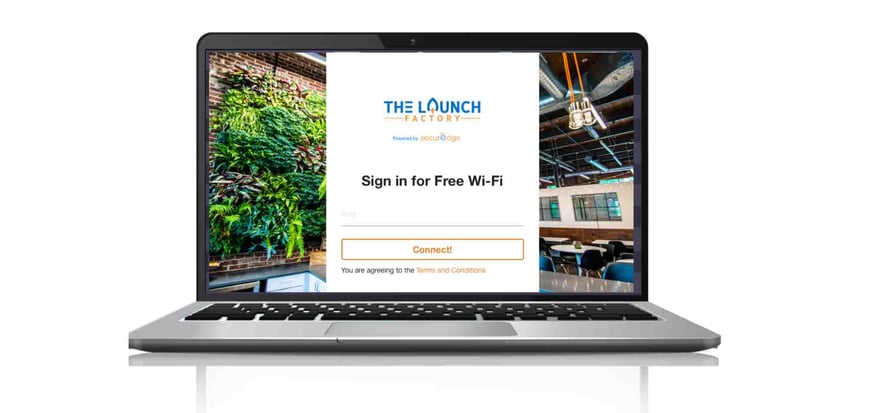
Here's three important reasons your guest wireless network needs to include a captive portal.
Creating an Online Business Identity
So users don’t connect to a hacker’s network:
One of the easiest ways hackers are stealing data today, is by posing as a legitimate wireless network.Once one of your guests or customers associates to it (logs into the fake network), the hacker has an easy way to grab their info.
So, if your business is a coffee shop or even a hospital providing guest WiFi access for your patients in the waiting room, your network should be properly identified to your end-users so they can avoid logging on to any potential fakes. It's important to be aware of someone setting up a wireless network nearby and calling it something similar to yours.
They may even call it “free public wifi” or something similar. The next time you’re at Starbucks look for the available WiFi networks in the area, chances are you’ve got someone close by looking to steal your data.
To Take Credit:
If you’re going through the hassle of providing a guest wireless network, you might as well let them know you did.
So throw up a page that has your logo and maybe even an offer for something that helps you better market your business and connect with your customers. Offer a coupon; ask them to connect with you on Facebook or twitter. These are all fantastic things for your business and can really make the cost of a guest WiFi network worth it.

Protecting your Business from Lawsuits:
Identity or Credit Card Theft:
Chances are you’re providing “open guest access” meaning you aren’t providing authentication of users and encryption of data. Simply put —the information the user is sending over the WiFi network is not secure.
That may seem logical and you may not think you have to tell the user not to send their credit card information over your wireless or use their social security number anywhere, but you do have to say that.You should require the user to check a box that says they understand that you aren’t liable if they do something stupid like sending their credit card information to a "spammy" website.
If your Guest or Customer does something illegal:
You know that the internet isn’t private right? The reality is, that when you buy internet access from a provider, they in-turn give you an IP Address. That it works just like a physical address to identify the location of where something is happening.
If someone is pirating music or movies from your network the companies looking to sue look for the “Source IP”, meaning they have the potential to track it to your location. We’ve actually been on college campuses when the IT Director is dealing with a threatening letter from the music industry. It can get nasty and you don’t want to be involved.
Captive Portals lets you include your rules into the terms of use policy, and force your guests to accept it. That will help you limit your liability for all of that bad stuff mentioned above. You may want to also consider using web filtering or application filtering software but that’s for another discussion.

Using Data to Improve the User Experience
Captive portals not only can provide you and your customers a safe and enjoyable wireless experience, they can also provide you with valuable data that you can then use to improve your services and products to ultimately create a better user experience.
How can you do this?
One of the easiest ways to do this is by allowing your guests to use their social login credentials on your captive portal to gain access to your network. In exchange for this option your guests will be authorizing you to have access to a variety of social data points.
For example, if someone using your captive portal logs in using their Facebook account, you could have permission to collect information such as, age, date of birth, what their interests are etc. With this information you can create more personalized experiences, based on real information. This is really the tip of the iceberg when it comes to business intelligence, but by using a simple captive portal you're much further along than you'd think.
If you have any questions about captive portals or network security, please contact us here.
*Editor's Note: This post was originally published in January 2012 and has been completely revamped and updated for accuracy and comprehensiveness.






